For this u need to create a 'autorun.inf' file in ur pendrive, and copy paste the contents as follows:
[AutoRun]
icon=iconsiconname.ico <---------path to ur icon
label=Saurabh's PD <---------name of ur PD
ShellOption1Command=Softwareanything.exe <---------path to software to run after autorun
If u dont have .ico file and u want to change ur .jpg file to .ico .Link to this:
http://www.prodraw.net/favicon/generator.php
Enjoy with ur customized Pendrive...
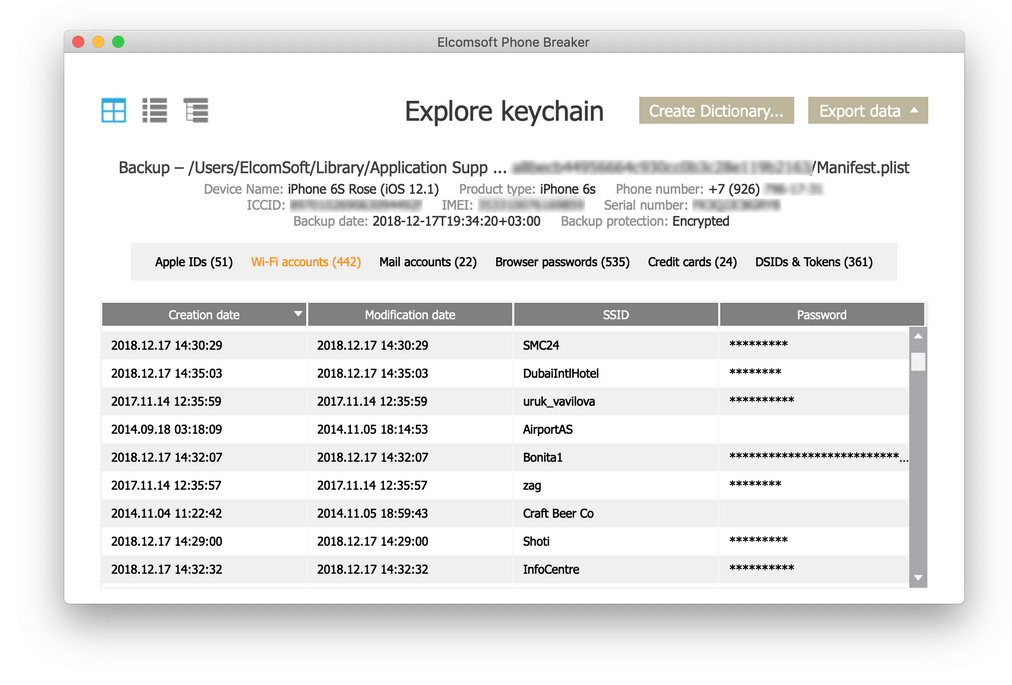
Keychain is the password manager Apple builds into its devices—iPhones, iPads, and Macs—to store users’ passwords, credit card details, Wi-Fi login details, and a host of other sensitive data.
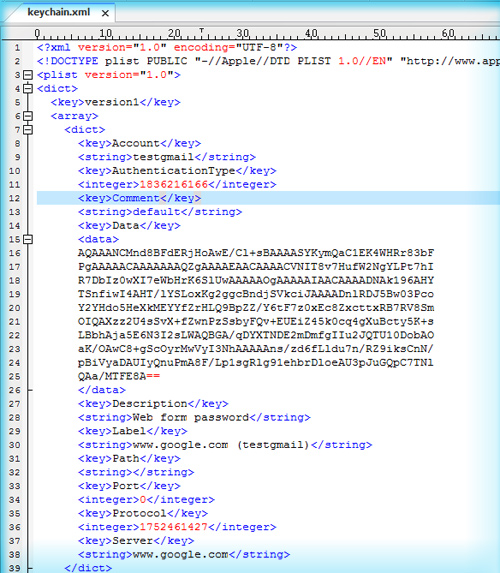
As shown in Figure 1, keychain services handles data encryption and storage (including data attributes) in a keychain, which is an encrypted database stored on disk. Later, authorized processes use keychain services to find the item and decrypt its data. Figure 1 Putting data and attributes into a keychain. Decrypt Keychain.plist 6,7/10 9514 votes Apr 11, 2012. This post details the step-by-step method required to extract a plist/OAuth token from a standard (non encrypted) iTunes backup of any iOS device.
At the same time, the utility is supposed to make it easy for users to create, recall, and access complex passwords.
Decrypt Keychain-backup.plist
Keychain is easily the most popular password manager used on iPhones, so keychain extraction is an incredibly important and useful capability for any digital forensic investigator or computer security researcher to have.
How does keychain work?

When a user inputs a password for a specific site or application, keychain (if enabled) offers to store the password and login details.
The utility also offers to generate strong passwords. Keychain does its best to prevent users from using the same passwords for their websites and applications.
Keychain stores the passwords and other sensitive details in iCloud and then syncs it across all the devices where the user is signed into and on which keychain is enabled.
This way, the user gets to access all their login data, credit card information, and other sensitive details from their iPhone, iPad, or Mac.
For example, a user can register an account for a site on his iPhone and later sign in to the same site on their Mac using the same login details. Keychain powers the fluid sign-in process across Apple devices.
How does keychain secure its data?
Keychain encrypts the stored passwords and credit card numbers with 256-bit AES, which is one of the most advanced encryption standards available.
The facility also employs end-to-end encryption tech and works to provide a device with a unique key and passcode. Only the user is supposed to know the passcode used to access keychain.
Users typically employ FaceID and TouchID (in place of their passcodes) to use keychain and view the passwords stored in it.
How can you use Belkasoft Evidence Center to extract keychain data from an iPhone?
Belkasoft Evidence Center is a digital forensics tool that investigators use to acquire, search, analyze, store, and share digital evidence from computers, smartphones, RAM, and cloud services.

The iPhone acquisition function based on checkm8 built into Belkasoft Evidence Center (or, in short, BEC) allows for full file system extraction. With this Belkasoft tool, digital forensic researchers and investigators are now extracting and analyzing different forms of data from iPhones.
To extract keychain data from an iPhone using Belkasoft, you have to perform these tasks:- Run the Belkasoft Evidence Center application on a PC.
- Go to the Add data source screen. Select Apple Checkm8.
- Connect the iPhone to the PC.
- Boot the iPhone into DFU mode. You can learn more about DFU mode here.
- Follow the on-screen instructions to use BEC to extract and analyze data from the iPhone.
- Go to the Passwords node (where the Keychain data is presented).
Decrypt Iphone Keychain-backup.plist
BEC also automatically decrypts applications data based on keychain. This way, for example, you can decrypt messages in the Signal app on an iPhone.
What devices are supported?
Keychain extraction is backed by the iPhone data acquisition function powered by checkm8, so you can use Belkasoft to extract keychain data from Apple devices equipped with the A7 chip through A11 SoC.
Here, we are referring to the generations of iPhones starting from iPhone 5s down till iPhone X.
Keychain data is actually just one of the many items that get extracted from a user’s iPhone. BEC provides forensically sound access to a wide range of encrypted information stored in iPhones.
To summarize things, we can say Belkasoft can reliably extract keychain data from an iPhone in either of these cases:
- The iPhone is one of the models that support checkm8 (as listed above) and you used the checkm8 function on it. In this case, the iPhone must be unlocked and you must know its passcode.
- The iPhone has been 'jailbroken' already. In this case too, the iPhone must be unlocked and you must know its passcode.
See also
- Belkasoft articles on checkm8 and other digital forensic issues